Remove Chimera Ransomware virus and restore files
Get rid of all components of the Chimera Ransomware virus and learn a workaround to recover encrypted data without having to pay the ransom to the criminals.
Keyloggers record their victims’ keystrokes, adware hijacks web browsers to serve ads, fake optimization programs attempt to trick people into buying their license, and ransomware infections encrypt users’ files to further extort money for decryption. Although this is certainly an oversimplified perspective of today’s malicious software scenery, the brief descriptions above suffice to figure out which category of threats poses the greatest risk. For the time being, the digital contagion calling itself the “Chimera® Ransomware” is on the list of emerging ransom Trojans showing a steady trend towards prevalence in its niche.
Chimera does not conceal its real gist and intensions, so there is hardly any manipulative component in its operation. The pest states upfront that it’s ransomware and that the user has fallen victim to it. The prevalent share of infected machines is currently concentrated in Germany, with an upward tendency of hitting other locations across the globe as well.
The attack is mainly pulled off through social engineering, where a person is duped into opening a contagious email attachment that contains a harmful executable under the guise of a regular PDF document or similar. Some compromise instances involve exploit kits that use the target system’s vulnerabilities to drop the payload. This scenario is usually deployed when a malicious or hacked site is visited, and the likelihood of noticing or preventing this type of assault is inappreciable.
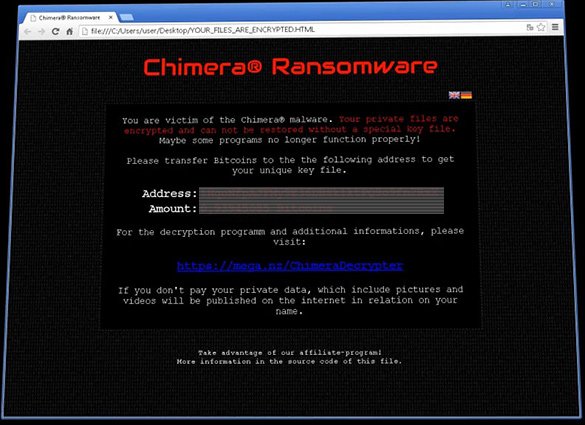
It takes Chimera Ransomware literally seconds to scan the hard drive on the plagued computer. It looks for items whose file extensions match a predefined array, which includes JPG, XLS(X), DOC(X), PPT(X) and many more. This way, the machine’s data structure is filtered by the criterion of personal and system-only objects. Every detected personal file is then encrypted with public-key, or asymmetric, cryptographic algorithm, which results in the victim’s incapability to open it. The virus will be henceforth opening a document named YOUR_FILES_ARE_ENCRYPTED.HTML each time Windows starts up. The same document is also added to every folder with hijacked files in it. This screen notifies the user what happened to their information and suggests that they submit a ransom in Bitcoin in order to get the private key and proceed with decryption. The price to pay is a little less than 1 Bitcoin (0.93945085 BTC, to be precise), which is about 230 USD. For further details and instructions, the malware recommends visiting an SSL protected page at Mega.nz/ChimeraDecrypter, whose digital certificate, by the way, is verified by Comodo.
The users who decide to pay the ransom are really on thin ice, because no one can possibly guarantee a favorable outcome of this deal. Removing Chimera Ransomware virus is not hard as long as reputable security software is used for this purpose. The next step is to try and restore the information that Chimera has rendered inaccessible – there’s a couple of options that can help achieve the desired result.
Chimera Ransomware removal with automatic cleanup tool
Note: removing Chimera is not that hard in itself. In fact, the virus may even self-destruct after the files have been encrypted, leaving the victim face-to-face with the upsetting ransom payment options. Anyway, the ransomware should be removed from the computer as it may get you infected with other cyber threats. An optimal cleaning workflow is to leverage a security application which will identify all potentially malicious software on your computer and handle it the right way. This approach ensures thoroughness of the removal and system remediation, and allows avoiding unintended damage that might occur as a result of manual malware deletion.
1. Download and install Chimera Ransomware removal software. Launch it and click the Start New Scan button. Wait for the application to check your computer for threats

Download Chimera Ransomware remover
2. When the app is done scanning your system, it will come up with an extensive list of detected objects. Click the Fix Threats option to have the utility completely remove this ransomware and affiliated infections found on your PC.
Alternative techniques to recover encrypted files
Given that Chimera Ransomware is an extremely complex and insidious malware, there is no guarantee that the files can be retrieved without submitting the Bitcoin ransom payment. There are some ways, however, that might be of help, even though they rely on a number of variables. Be sure to try the methods below.
1. Data backups
If you have been backing up your information, to the cloud for instance, you’re a lucky person. Just get the data restored using the respective features. It’s too bad not that many people can boast such prudence. All in all, this is the best case scenario.
2. Shadow Volume Copies
Even though Chimera Ransomware tends to erase all Shadow Volume Copies of files on the compromised workstation, it might not cope with this task. If that’s the case, chances are you can recover your information. Note that this approach is applicable only if you had System Restore activated prior to the infection. Also, the files you can restore this way may not necessarily be the latest versions. Make sure you try one of the following methods though:
- Take advantage of Previous Versions
If you right-click a random file on your PC and select Properties in the drop-down menu, you will see the Previous Versions tab at the top of the window. Once you hit that tab, the operating system will display a list of file versions corresponding to the restore points that were made. Select the most recent one and click Copy to restore the file to a new location, or pick Restore to recover it to the directory it was originally in.
- Use ShadowExplorer app
The routine above can be accomplished with a tool designed specifically to restore Shadow Volume Copies for files and folders. To move on, download ShadowExplorer to your computer, install and launch it. Using the features in the top left-hand part of the GUI, select the drive name and the date. Rick-click on the file or folder you would like to be restored and choose Export.
3. File recovery tools
This ransomware deletes the original data objects, encrypting their copies instead. Since Windows still stores these eliminated items, which is common knowledge, why not try to recover them using software that was created for this purpose? One of the applications capable of doing this is Data Recovery Pro. Run the tool and see if it can pull your removed data out.
Double-checking never hurts
Last but not least, a quick reminder: the removal of Chimera Ransomware from a compromised system doesn’t mean the files will get decrypted. To try to recover your data, stick to the methods above. That notwithstanding, since the ransomware proper is dangerous it must be exterminated for good. To make sure the virus has been removed, consider running an additional security scan as a completion of the cleanup procedure.

Download and install Chimera removal software


Leave a Reply