.Java ransomware: how to decrypt {badfail@qq.com}.java files
Get an effective way to restore .java extension files encrypted by the latest variant of the CrySiS ransomware and remove the perpetrating program for good.
In light of the cryptojacking craze invading the digital world with astonishing rapidity, the ransomware economy has been losing top positions on cybercriminals’ agenda. Some online extortionists have called it quits and switched to other moneymaking vectors, while few persist in their efforts to move on with the blackmail activity. The CrySiS, or Dharma, ransomware developers are in the latter category. They keep releasing new editions of their ransom Trojan on a regular basis, and have managed to occupy a niche somewhere at the peak of this underground ecosystem. Their latest contrivance is referred to as the .java ransomware due to the .java extension being appended to every file it encrypted.
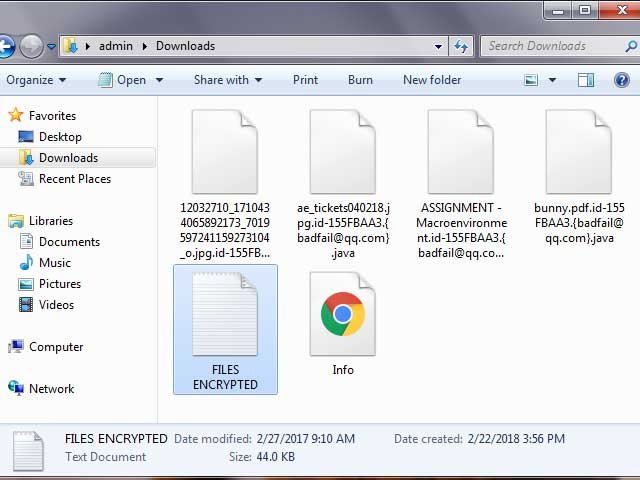
There are more tweaks being made to filenames, though. The Java ransomware concatenates a string to each one in the following format: id-[victim ID].{attacker’s email}.java. Consequently, a file named Sample.jpg turns into something like Sample.jpg.id-155FBAA3.{badfail@qq.com}.java. The email address can be in curly braces, as in the example above, or in square brackets. Furthermore, there are multiple addresses used by different affiliates distributing the pest, including faremar@cock.li, black.mirror@qq.com, 1778357646@qq.com, chivas@aolonline.top, sm@uwmanage.com, saruman_saruman@aol.com, and habibi.habibi3@aol.com.

In order to alert the victim and explain how the hostage data can be decrypted, the .Java ransomware drops a combo of ransom notes onto the contaminated host, namely on the desktop and inside encrypted folders. These are objects named Info.hta and FILES ENCRYPTED.txt. The former (see screenshot above) pops up automatically when the plagued computer loads. The how-to’s instruct the user to contact the adversary by sending an email to the specified email address, where they should provide their unique ID. In addition to that, the crooks claim to allow restoring up to five files for free. These items should neither contain valuable information nor exceed 10 MB in size. The black hats will respond to the message with their Bitcoin wallet address and the amount of cryptocurrency to submit for the private decryption key. The size of the ransom is in the range of 0.1-0.2 BTC.
The Java ransomware version of CrySiS/Dharma strain still circulates by means of exploiting hacked RDP connections. The ill-minded operators use brute force or dictionary attacks to obtain credentials for one’s remote desktop services and, in case of success, execute the malicious binary on the machine manually. The rule of thumb, therefore, is to disable RDP when not in use, and never keep the default access details. When hit by the .java files virus, be sure to start with troubleshooting with the steps below.
Java ransomware removal with automatic cleanup tool
Note: removing the Java/CrySiS blackmail malware is not that hard in itself. In fact, the virus may even self-destruct after the files have been encrypted, leaving the victim face-to-face with the upsetting ransom payment options. Anyway, the ransomware should be removed from the computer as it may get you infected with other cyber threats. An optimal cleaning workflow is to leverage a security application which will identify all potentially malicious software on your computer and handle it the right way. This approach ensures thoroughness of the removal and system remediation, and allows avoiding unintended damage that might occur as a result of manual malware deletion.
1. Download and install Java ransomware removal software. Launch it and click the Start New Scan button. Wait for the application to check your computer for threats

Download Java ransomware remover
2. When the app is done scanning your system, it will come up with an extensive list of detected objects. Click the Fix Threats option to have the utility completely remove this ransomware and affiliated infections found on your PC.
Alternative techniques to recover encrypted files
Given that the .Java ransomware is an extremely complex and insidious malware, there is no guarantee that the files can be retrieved without submitting the Bitcoin ransom payment. There are some ways, however, that might be of help, even though they rely on a number of variables. Be sure to try the methods below.
1. Data backups
If you have been backing up your information, to the cloud for instance, you’re a lucky person. Just get the data restored using the respective features. It’s too bad not that many people can boast such prudence. All in all, this is the best case scenario.
2. Shadow Volume Copies
Even though the Java ransomware tends to erase all Shadow Volume Copies of files on the compromised workstation, it might not cope with this task. If that’s the case, chances are you can recover your information. Note that this approach is applicable only if you had System Restore activated prior to the infection. Also, the files you can restore this way may not necessarily be the latest versions. Make sure you try one of the following methods though:
- Take advantage of Previous Versions
If you right-click a random file on your PC and select Properties in the drop-down menu, you will see the Previous Versions tab at the top of the window. Once you hit that tab, the operating system will display a list of file versions corresponding to the restore points that were made. Select the most recent one and click Copy to restore the file to a new location, or pick Restore to recover it to the directory it was originally in.
- Use ShadowExplorer app
The routine above can be accomplished with a tool designed specifically to restore Shadow Volume Copies for files and folders. To move on, download ShadowExplorer to your computer, install and launch it. Using the features in the top left-hand part of the GUI, select the drive name and the date. Rick-click on the file or folder you would like to be restored and choose Export.
3. File recovery tools
This ransomware deletes the original data objects, encrypting their copies instead. Since Windows still stores these eliminated items, which is common knowledge, why not try to recover them using software that was created for this purpose? One of the applications capable of doing this is Data Recovery Pro. Run the tool and see if it can pull your removed data out.
Double-checking never hurts
Last but not least, a quick reminder: the removal of Java ransomware from a compromised system doesn’t mean the files will get decrypted. To try to recover your data, stick to the methods above. That notwithstanding, since the ransomare proper is dangerous it must be exterminated for good. To make sure the virus has been removed, consider running an additional security scan as a completion of the cleanup procedure.

Download and install Java/CrySiS ransomware removal software


Why would I trust you? This info is unsolicited, how do I know you aren’t the bad guys?
Does this really work?